I’ve wondered this for a while (especially when it comes to the private sector job market).
Few Interesting Findings From Analyzing Data:
- ~1% of Global LinkedIn computer security related profiles mention memory corruption terms ( 22K/1.950M)
- ~1% of US LinkedIn computer security profiles mention memory corruption terms (11K/909K)
- ~501 Researches have submitted Memory Corruption bugs to ZDI & Microsoft between 2018 and 2021.
The Data
The asterisked categories in the below graph are likely high-quality counts for estimating number of people writing memory corruption exploits. Overlap is expected between groups.
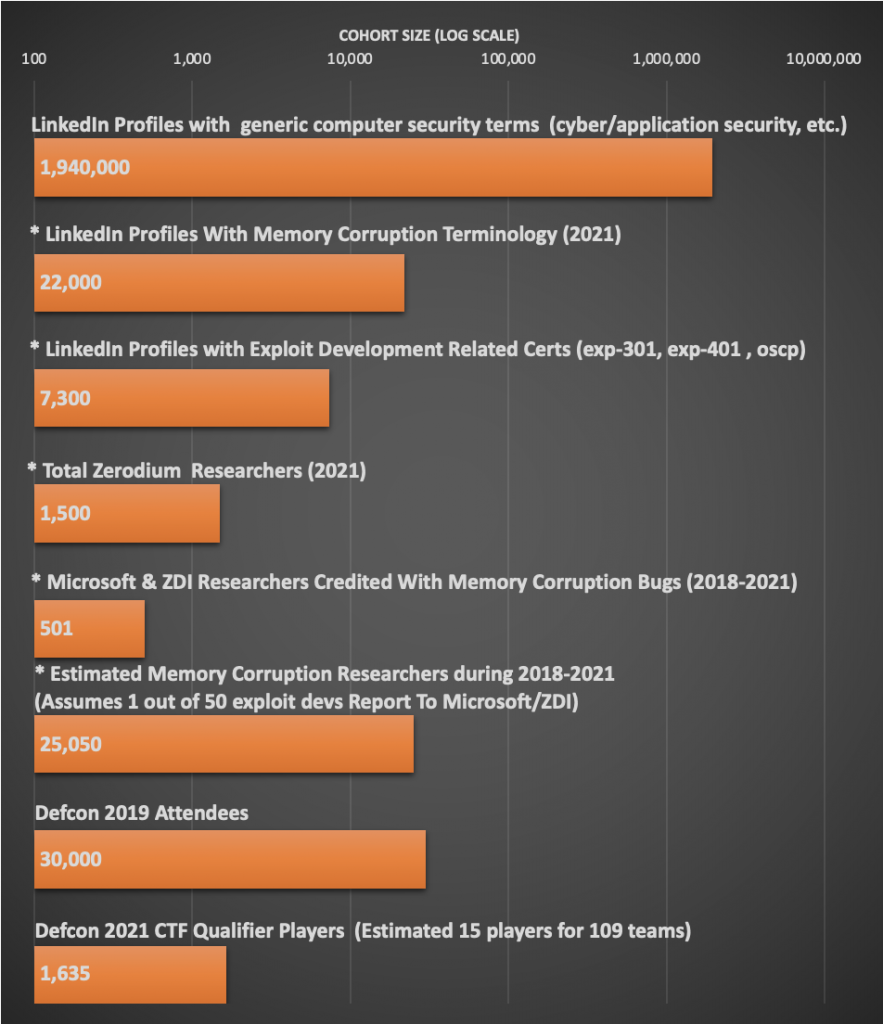
Collected Data:
| Population | Population Size |
| LinkedIn
Profiles mentioning computer security terms (cyber/network/red team/application/offensive/penetration security ) | 1,940,000 |
| * LinkedIn Profiles With Memory Corruption Terminology (2021) | 22,000 |
| *
LinkedIn Profiles with Exploit Development Related Certs (exp-301, exp-401 , oscp) | 7,300 |
| * Total Zerodium Researchers (2021) | 1,500 |
| * Microsoft & ZDI Researchers Credited With Memory Corruption Bugs (2018-2021) | 501 |
| *
Estimated Memory Corruption Researchers during 2018-2021 (Assumes 1 out of 50 exploit devs Report To Microsoft/ZDI) | 25,050 |
| Defcon 2019 Attendees | 30,000 |
| Estimated
Defcon 2021 CTF Qualifier Players (Includes 109 teams that had > 0 points. Guessed 15 Members Per Team) | 1,635 |
Data Sources:
- Defcon 2019 Transparency Report [link]
- LinkedIn search for computer security profiles (“network security” OR “computer security” OR “cybersecurity” OR “cyber security” OR “red team” OR “offensive security”). Couldn’t add additional terms such as “Cloud Security” and “Application Security” as LinkedIn was erroring out due to to number of OR operators. [link]
- LinkedIn search for memory corruption mentions in profiles (“use-after-free” OR “use after free” OR “buffer overflow” OR “memory corruption” OR “fuzzing” OR “exploit development”). *Stack overflow not searched for as stackoverflow.com likely to be matched. “Heap Corruption” and “Heap Overflow” did not have findings. [link]
- Microsoft Security Acknowledgements Section [link]
- ZDI Public Advisories Data [link].
- ZDI reports more than half vulnerabilities in 2019 [link]
- ZDI has 9,000+ contributors [link]
- CTF Time 2021 Team Listing [link]
- Zerodium Research Count is mentioned on home page [link]